access control with ease
Prevent unauthorized facility entry by pre-verification of visitors’ identities through nPKD database and biometry data checks.
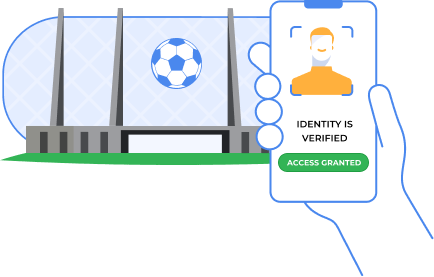

Protect audience on events
Prevent unauthorized facility entry by cross-checking identity document data against the government’s nPKD database and verifying biometry data.
Designed to protect
Verify with Confidence
NFC-based validation through Public Key Directory protects from document forgery.

Minimize delays
Verification process takes seconds, ensuring swift entry without compromising safety.

Apply custom watchlists
Choose from internationally recognized watchlists by Refinitiv or create a custom watchlist using your data.
The Workflow

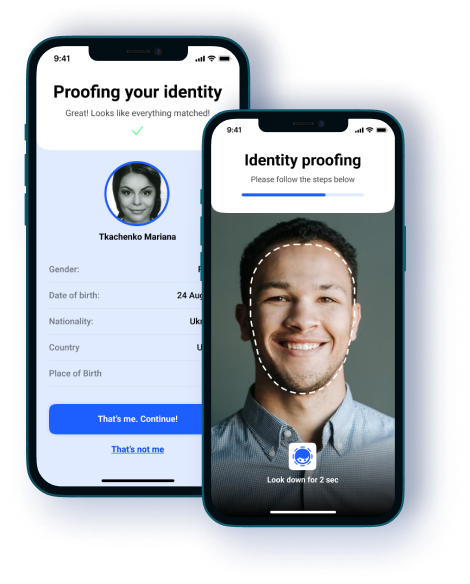
Pre-verification
Visitors provide identity information to verify. On average, it takes 60 seconds to finish it. This pre-verification allows us to filter unwanted visitors and create a safe space for others

Pre-verification
Visitors provide identity information to verify. On average, it takes 60 seconds to finish it. This pre-verification allows us to filter unwanted visitors and create a safe space for others
At the entrance
Before entering the stadium, they need to scan a QR code on a display. Afterwards, they pass a liveness verification to confirm their facial photo identity in real time.
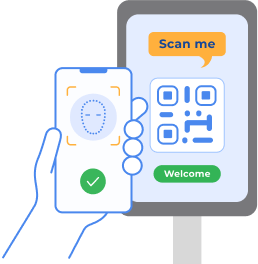

At the entrance
Before entering the stadium, they need to scan a QR code on a display. Afterwards, they pass a liveness verification to confirm their facial photo identity in real time.

Communicating with hardware
Our API communicates with your hardware, responding to whether the verification passed successfully or not.

Communicating with hardware
Our API communicates with your hardware, responding to whether the verification passed successfully or not.
See how Mob.id manages access to a facility
Review the presentation to learn how Mob.id achieves the right level of security improving user experience.

See how Mob.id manages access to a facility
Review the presentation to learn how Mob.id achieves the right level of security improving user experience.
See how Mob.id manages access to a facility
Review the presentation to learn how Mob.id achieves the right level of security improving user experience.

secure and reliable

Secure System
Mob.idʼs PKI serves as a security layer that adds complexity for potential fraudsters, effectively thwarting attempts by portable hacking devices like Flipperzero.
Instant Validation
We ensure that even sophisticated attempts by malicious individuals are unsuccessful. This approach prevents using fake masks or 3D face models to breach the system.

Threat Detection
Mob.id stands ready to block access whenever an individual in the watchlist seeks entry to the facility.
testimonials
Mob.id team helped us to identify the problems with the current authorization of my employees. In the end, we got a transparent process where the compliance officer can track each login and ensure that no one except managers has access to the admin section.
Jan Willem Tromp
Mob.id team helped us to identify the problems with the current authorization of my employees. In the end, we got a transparent process where the compliance officer can track each login and ensure that no one except managers has access to the admin section.
Process visitors with confidence.
We thrive on challenges and are committed to providing the level of protection you desire.
Schedule a call with us to explore the full potential of Mob.id and discover how it can meet your unique security needs.
Trusted partners

Start using Mob.id now
1. Review the documentation and set up the call with our back-end team.
2. We provide the license for the organization to get ready to assist your clients.
3. Clients can start using API or mobile SDK for their businesses.
Trusted partners